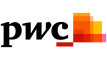
Integrating key threat- management tools in the cloud Many organizations are proactively adopting or updating key technologies that are essential to gathering and analyzing threat intelligence. Increasingly, they are opting for cloud-based managed security services rather than traditional on-premise systems. In fact, 62% of respondents use managed security services for initiatives like authentication, identity and access management, real-time monitoring and analytics, and threat intelligence. Threat detection tools and processes in place, 2016 52% 51% 48% 47% Have intrusion- Actively monitor & Conduct Conduct detection tools analyze information vulnerability threat security intelligence assessments assessments 47% 45% 44% Have security Use threat Conduct information & intelligence penetration event management subscription tests (SIEM) tools services Source: PwC, CIO and CSO, The Global State of Information Security® Survey 2017, October 5, 2016 7 Key findings from The Global State of Information Security® Survey 2017 © 2016 PwC
 Toward new possibilities in threat management Page 7 Page 9
Toward new possibilities in threat management Page 7 Page 9